Best practice for using userAccountControl in scoping
Learn how to effectively utilize the UserAccountControl attributes to enhance the robustness of your complex expressions.
Table of Contents
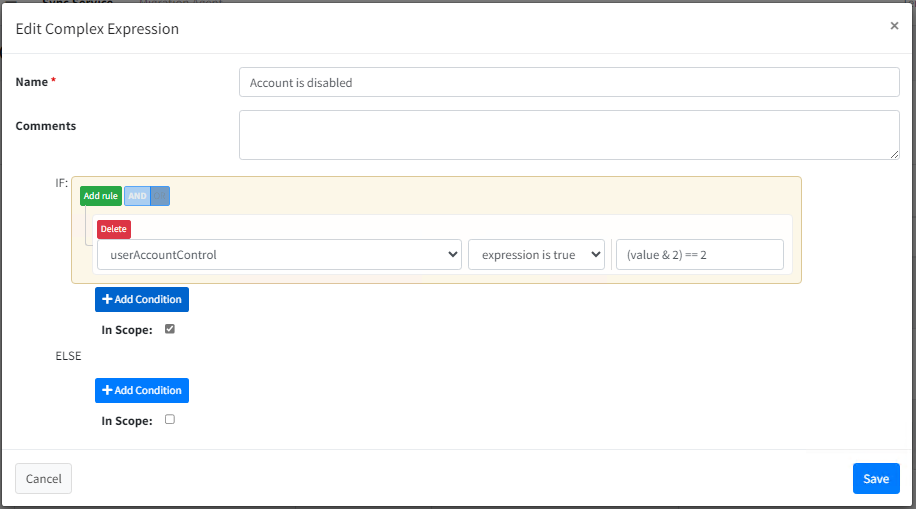
A robust and more reliable way to identify the userAccountControl state in scoping is by using its property flags in your complex expression.
For example, if you want to scope on the userAccountControl attribute to 0x0202 in hexadecimal (0x002 + 0x0200) in decimal, it's 514 (2 + 512) = ACCOUNTDISABLE, you would use the decimal value 2. (you can review the decimal values in the Microsoft article below)
Attribute: UserAccountControl
Logic: “expression is true”
Value: (value & 2) == 2
NOTE: if an account is moved out of scope because of a state change, check your config to ensure all circumstances are accounted for, for example, you may not want the account deleted from the target if it becomes disabled. The “what if” feature is your friend here.
Your own research
Microsoft provide more details on the values here.
UserAccountControl property flags - Windows Server | Microsoft Learn
There are further hexadecimal value states here
Understanding the UserAccountControl Attribute in Active Directory - Microsoft Community Hub
Examples of other important attributes
Active Directory (AD) attributes that use hexadecimal values are primarily those that involve unique identifiers, security settings, timestamps, and specific configurations.
Below are some of the key AD attributes that typically use or display hexadecimal values, they will not all conform to the same values as userAccountControl, each have their own newances.
objectGUID:
- Description: A globally unique identifier for the object.
- Hexadecimal Format: It is a binary large object (BLOB) and often represented as a hexadecimal string.
objectSID:
- Description: Security Identifier for the object.
- Hexadecimal Format: It is stored as a binary value and often displayed in hexadecimal.
userAccountControl:
- Description: Flags that control the behaviour of user accounts.
- Hexadecimal Format: Often represented in hexadecimal to denote various control flags.
pwdLastSet:
- Description: The timestamp for the last password set.
- Hexadecimal Format: While it represents a timestamp, it is often displayed in hexadecimal in certain tools.
unicodePwd:
- Description: Encrypted password of the user.
- Hexadecimal Format: Stored in an encoded format that is often shown as hexadecimal.
supplementalCredentials:
- Description: Stores additional credential information for the user.
- Hexadecimal Format: Typically stored in a binary format, displayed as hexadecimal.
logonHours:
- Description: Specifies the hours during which the user is allowed to log on.
- Hexadecimal Format: Represented as a bit string, often shown in hexadecimal.
userParameters:
- Description: Stores user-specific configuration data.
- Hexadecimal Format: Encoded in a format that may be displayed as hexadecimal.
msDS-KeyVersionNumber:
- Description: Indicates the version number of the key.
- Hexadecimal Format: Stored and displayed in hexadecimal format.
ms-Mcs-AdmPwd:
- Description: Stores the password for the local administrator account (used by LAPS).
- Hexadecimal Format: Stored in a secure format, often represented in hexadecimal.
ntSecurityDescriptor:
- Description: Contains the security descriptor for the object.
- Hexadecimal Format: Stored as a binary value, often shown in hexadecimal for analysis.
replUpToDateVector:
- Description: Used in replication, stores the highest update sequence number (USN) applied from each replication partner.
- Hexadecimal Format: Stored as a binary value, often represented in hexadecimal.
These attributes are essential for various administrative and security-related functions in Active Directory. The hexadecimal representation helps in standardizing and simplifying the storage and display of complex binary data.